

Wyze security
Here you can find information regarding Wyze account and data security. At Wyze, we put immense value in our users’ trust in us. This site clarifies our security measures, shares best practices to help ensure your account remains secure, and hosts an FAQ section.
Since the founding of Wyze, we have existed for our users. The promise and dream to build a company serving our community is a core part of Wyze. This site helps advance that promise and we want to thank you for joining us.
-

Report Suspicious Activity
Make a report -

Vulnerability Disclosure Program
Learn more -

Wyze Bug Bounty Program
Join the hunt -

Keep your account secure
Learn more
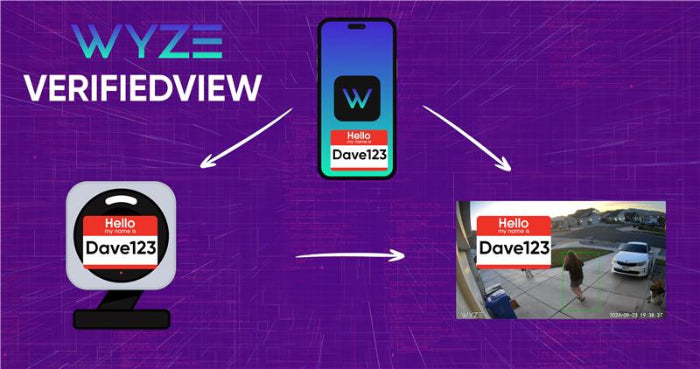
VerifiedView
A new security feature that embeds a hashed user ID into every video, photo, and livestream captured by Wyze cameras. This ensures only the rightful account owner can access or view their content, adding an extra layer of protection beyond passwords and encryption. The feature rolls out automatically with app and firmware updates and requires no user action, serving as a behind-the-scenes safeguard to prevent unauthorized access even in rare security failures.
Developed with layers of security
Our cameras, smart devices, and Wyze app are meticulously designed with multiple layers of security to help give you peace of mind. Your safety is our priority.
We participate in industry best practices to keep you safe. These best practices include the following:
- ioXt certified for iOS & Android, leading connected device security certification
- Certified by Google MASA for Android
- Passing NCC penetration testing
- Passing 3rd-party security testing for hardware with ReFirm Labs
- Bitdefender indepth pentesting for Camera V3
- Using AWS infrastructure (SOC2 & ISO compliance)
- Implementing Lacework to enhance the security of our cloud infrastructure
- Wyze mandated 2-factor authentication for all customers
- Wyze utilizes the latest Amazon security protections including AWS WAF, GuardDuty services.
This list continues to go on depending on our device. For example, we have UL/FCC/Energy Star certificates for our light bulbs.

Your data is never sold
We do not sell your data for money. Wyze does not sell your personal information in the conventional sense (i.e., for money). It's that simple. Your privacy is a big deal for us – a key part of being friends with our customers.
Wyze may disclose certain data points about you such as your activities on our website or app to service that allow us to show you interest-based advertisements, or to our business partners. Making this information available to these companies may be considered a “sale” under the California Consumer Privacy Act (CCPA) or other state privacy laws. To learn more about how we collect, use and disclose your personal information, please review our Privacy Statement.

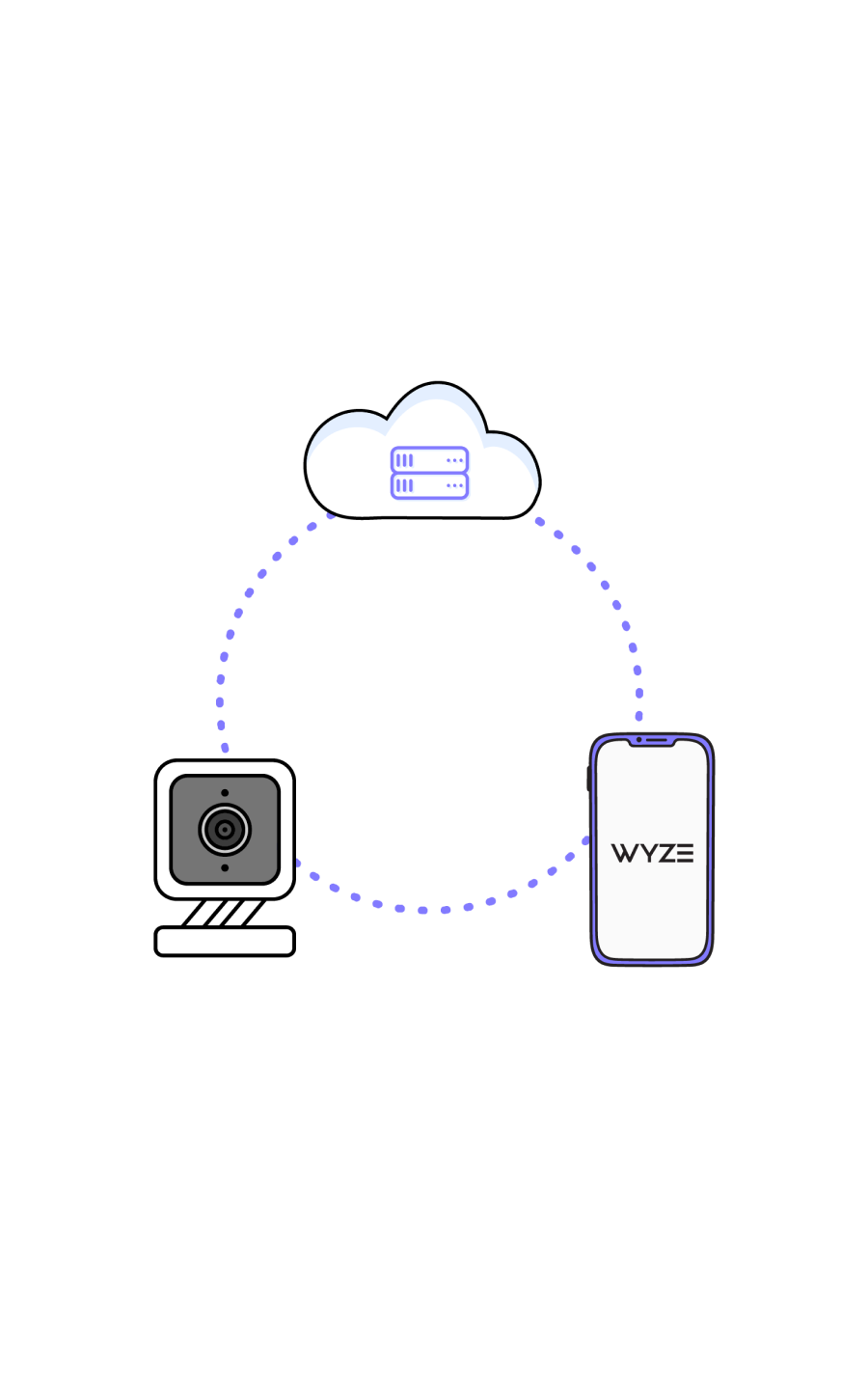
Live stream and video encryption security
The communication requests between your mobile device, your Wyze product, and the AWS Cloud Server are made via https (Transport Layer Security, also known as TLS) for Event videos.
We use symmetric and asymmetric encryption, consistent hashing, and other ways to help ensure users’ information cannot be stolen. Each camera has its own secret key and certificate so that we can validate its identity during handshake. The contents are encrypted via AES 128-bit encryption to protect the security of the live stream and playback data.
During the connection process, every device in the process has its own secret key and certification, so that we can validate their identity during handshake. Even if a hacker intercepts the data package, the data cannot be decrypted.
The best partners & practices
-

Amazon Web Services (AWS)
-
ioXt Certified (iOS & Android)
-
AES 128-bit encryption
-

Two-Factor Authentication
-

Shopify Shop Platform
-

Monitoring & Detection
Security Metrics certificate
Tested quarterly to ensure that high security standards are maintained, which significantly reduces the risk that this site will be compromised.
View current certificate
View our privacy statement
This is the very detailed legal documentation that you can review. Grab a coffee and toss that new book to the side. You're in for a solid read.
Learn more
Tips to keep your account secure
We'll show you steps you can take to make your account even safer. From choosing a strong password to enabling Two-Factor Authentication (2FA).
Learn more
Security advisory
Stay informed with our security alerts and updates in our official forum thread. Get the details in our community.
Learn more
Device Sharing Permissions
When you share a Wyze device, the invited user can use most daily features of the product. Some management and configuration functions are reserved for the owner of the device.
Learn more
Security & Trust
FAQs
The communication requests between your mobile device, your Wyze product, and the AWS Cloud Server are made via https (Transport Layer Security (TLS)) for Event videos.
We use symmetric and asymmetric encryption, consistent hashing, and other ways to make sure users’ information cannot be stolen. Each camera has its own secret key and certificate so that we can validate its identity during handshake. The contents are encrypted via AES 128-bit encryption to protect the security of the live stream and playback data.
During the connection process, every device in the process has its own secret key and certification, so that we can validate their identity during handshake. Even if a hacker intercepts the data package, the data cannot be decrypted.
With Wyze Cam, users can view camera videos using two methods: live streaming and recorded videos. Streaming is encrypted during transfer from device to phone. Camera videos are transferred under a secure channel from device to Wyze Cloud (ingestion) and from Wyze Cloud to phone (digestion).
Wyze employees do not have the ability to view a user’s camera’s live feed. This is because we use a P2P live streaming solution, which establishes a direct connection between the phone and the camera. While this is a technical solution to privacy, we also have a policy at Wyze prohibiting employees from viewing live streams.
Event videos, which are videos recorded when motion or sound is detected, are securely uploaded to the Wyze AWS server. From here, the video only would be accessed with permission from executive-level Wyze managers in extremely rare or severe cases, such as if Wyze were to be presented with a court subpoena. No other Wyze employees have access to these videos.
Creating a strong password is the first line of defense while you’re registering (or updating) your Wyze account. We recommend a password with a combination of uppercase and lowercase letters, numbers, and symbols. You can also use a password management tool to help use unique passwords for different websites and accounts.
When choosing a password, avoid using personal information like birthdays, first and last names, and well-known words or phrases from movies, shows, books, or music. Sequenced numbers (12345) and letters (abcde) are also easier for hackers to crack, so avoid using these as well. Change your password often, but be sure that it’s unique and not recycled.
Consider intentionally misspelling words by substituting numbers and letters with symbols to make it more complicated for a hacker to guess. For example → f0R_3x@mP1e!. Be aware that some symbols will be more difficult to enter using a smartphone.
Two-factor authentication is a method of securing your account with a secondary authentication token, or code. This secondary token is generated after you enter your email and password, and is a requirement to sign in as long as 2FA is enabled on your account.
There are two secondary authentication methods available:
- Text message (SMS): Sends a text to your phone containing the associated key or code.
- Authenticator app: Pairs to your account, then continually generates codes on a short timer which act as the needed key.
In the Wyze app, tap Account > Security > Two-Factor Authentication. Then tap Verification by SMS (text message), and follow the prompts to add and verify your phone number.
Once SMS 2FA is enabled, you must enter the verification code sent by SMS to your primary (or backup) phone number when logging into your account.
In the Wyze app, tap Account > Security > Two-Factor Authentication. Then tap Verification by Authenticator app, and select the authentication app you prefer.
Copy the key generated from the Wyze app and paste it into your selected authenticator app. Verify the 6-digit code generated by entering it in your Wyze app. Make sure you save the recovery code shown at the end of setup.
Once TOTP 2FA is enabled, you must enter the time-sensitive verification code displayed in your authentication app when logging into your account.
Never share your Wyze account credentials with anyone you do not trust completely with your account. If you do, they’ll be able to access and change your details - even your password - without your permission.
Instead, ask your friends and family to create their own free Wyze account so you can share devices with them without compromising your login credentials. For more information on the Sharing feature, check out How to Use Sharing.
Note: Wyze employees will never request your password under any circumstances.
Never share your Wyze account credentials with anyone you do not trust completely with your account. If you do, they’ll be able to access and change your details - even your password - without your permission.
Instead, ask your friends and family to create their own free Wyze account so you can share devices with them without compromising your login credentials. For more information on the Sharing feature, check out How to Use Sharing.
Note: Wyze employees will never request your password under any circumstances.
Outside the app, Wyze will only contact you using the following official channels:
- @wyze.com
- @support.wyzecam.com
- @forums.wyzecam.com
If you reach out to Wyze, there will be circumstances when an employee may request information to help with your case.
Wyze employees may ask for:
- You to send us an email from the email address associated with your Wyze account
- A screenshot of the in-app Device Info screen to verify IP/MAC or a photo of the sticker on the device
- Recordings or screenshots of product pages, or sample video recordings to help troubleshoot visual and audio issues
- Your shipping address for returns, replacements, and sending out testing units
Wyze employees will never ask for your:
- Full credit card number (we only may ask for the last 4 digits)
- Wyze account password
- Social Security Number (SSN)

